In the last few years, a family of new security vulnerabilities was discovered affecting many CPUs made by all major CPU makers. Sadly, patching these vulnerabilities had the side effect of a huge performance impact that can reach up to a ~%25 decrease in some workloads.
New CPUs (mostly the ones released after 2020) often do not suffer from such vulnerabilities nor from the highly performance-impacting patches to fix them. However, for a lot of older CPUs, your Linux system performance may be taking a considerable performance penalty to remain secure from such vulnerability exploits.
Table of Contents:
Turning Off CPU Mitigations on Linux for Performance
These CPU mitigations are enabled by default on all Linux distributions, and for a good reason: Without them, any hijacked software component on your OS can be used to escalate privileges or access protected areas of your computer memory and retrieve sensitive information.
Should You Disable CPU Mitigations?
It depends on the CPU you are using, the possible performance gains, and your threat factors.
According to our good friends at Phoronix’s benchmarks, CPUs such as Intel’s 12th generation CPUs would gain less than 1% of extra performance when CPU mitigations are turned off. Furthermore, some CPUs like those in the AMD 7000 series can actually give a worse performance if mitigations are turned off.
In such cases, you should not bother with turning off CPU mitigations at all.
However, for older CPUs such as those based on AMD Zen 1 and Zen 2 architectures, or Intel CPUs earlier than the 9th generation, the impact can reach up to 25% in some cases:
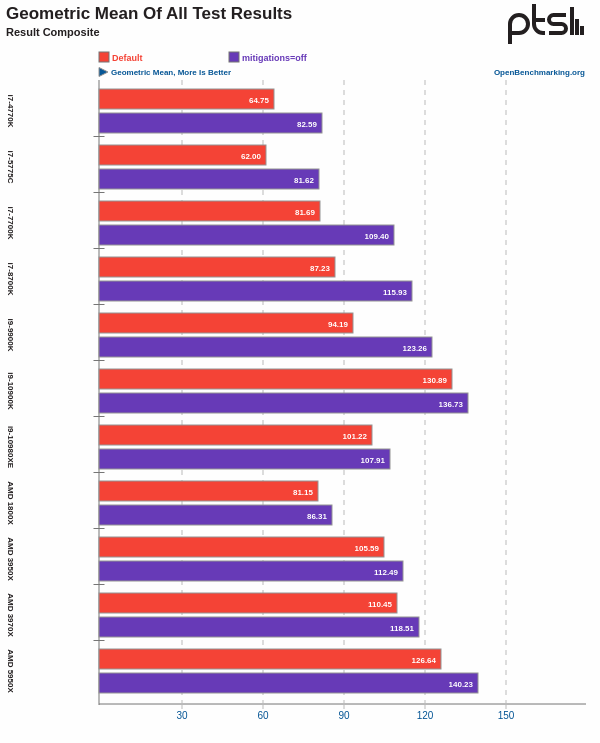
If you own such a CPU in your computer, then perhaps it can be worth it, depending on your possible threat factors.
If you are an advanced Linux user who knows how to harden his/her OS, always uses software from trusted channels, deals with few to no external 3rd-party possible exploitable files, and has a good awareness of the security aspects of your Linux system, then you may go for it.
However, if you just happen to stumble upon this article from search engines or social media, and don’t really understand what possible threats you are enabling on your system by turning off CPU mitigations, then absolutely do not follow this guide.
Basically, this guide is for desperate people who are stuck with using an older CPU that is taking a huge impact from CPU mitigations while mostly doing their computing tasks in a safe and isolated matter. While nothing is perfectly safe, and these CPU mitigations can even be triggered via web browser vulnerabilities, the final choice is always up to you.
Proceed at your own guarantee.
How to Disable CPU Mitigations on Linux
In general, the way to disable CPU mitigations on Linux is by adding the mitigations=off parameter into your GRUB parameters so that the kernel no longer loads these patches.
For Debian-based and Ubuntu-based distributions, you will need to edit the /etc/grub/default file and append that parameter into your kernel boot options like the following picture (at the end of the GRUB_CMDLINUX_LINUX_DEFAULT line):
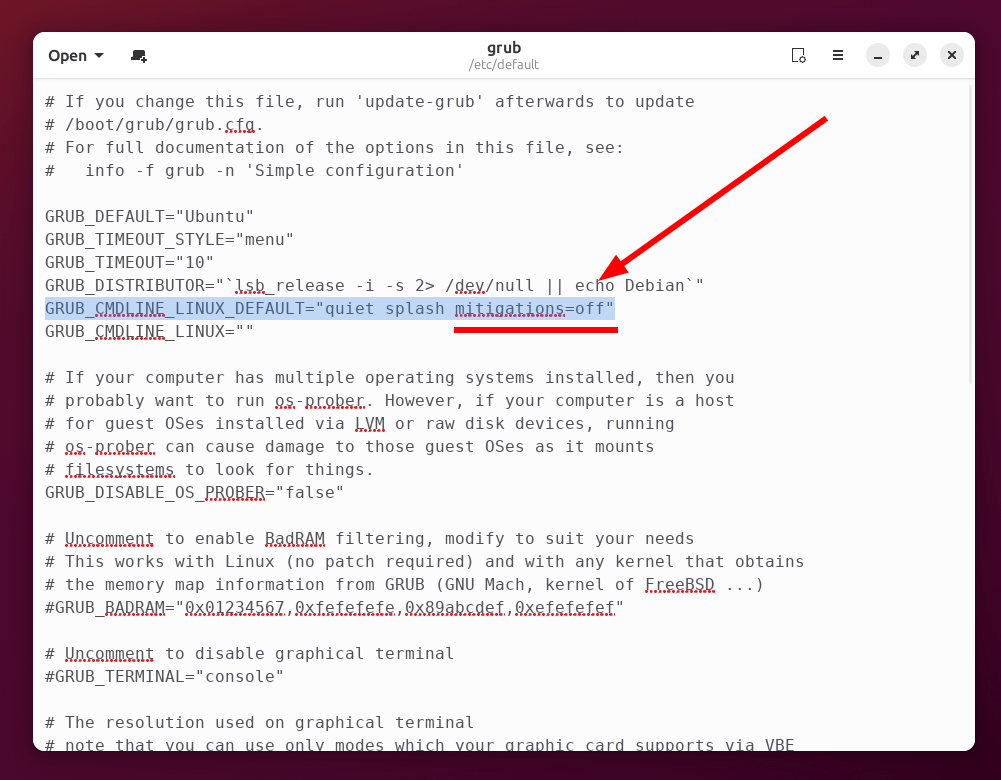
Save the file, exit, and reboot for changes to take effect.
For Fedora-based distributions, you can run the following command to disable them:
sudo grubby --update-kernel=ALL --args="mitigations=off"
For other Linux distributions, just find the location of your GRUB configuration file and edit the boot parameters as we explained earlier.
It is also possible to disable some specific CPU mitigations if you like; instead of disabling all of them, you may test your CPU to see which ones affect its performance the most and disable those only. The full documentation on what parameters to use instead of mitigations=off are available on the kernel website and are given in a special page for each possible hardware vulnerability.
Check if CPU Mitigations are Turned off
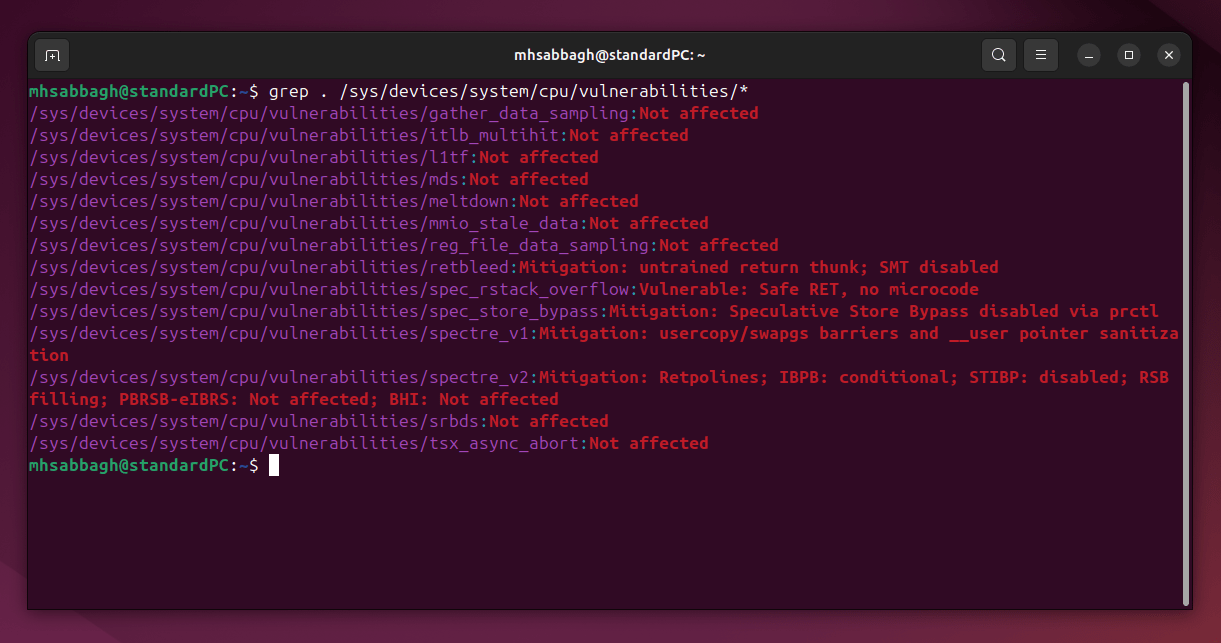
The following command can be used to check whether CPU mitigations are turned on or off on your Linux system:
grep . /sys/devices/system/cpu/vulnerabilities/*
Before turning them off, the output of the previous command would look like the following:
After turning them off, it would look like this:
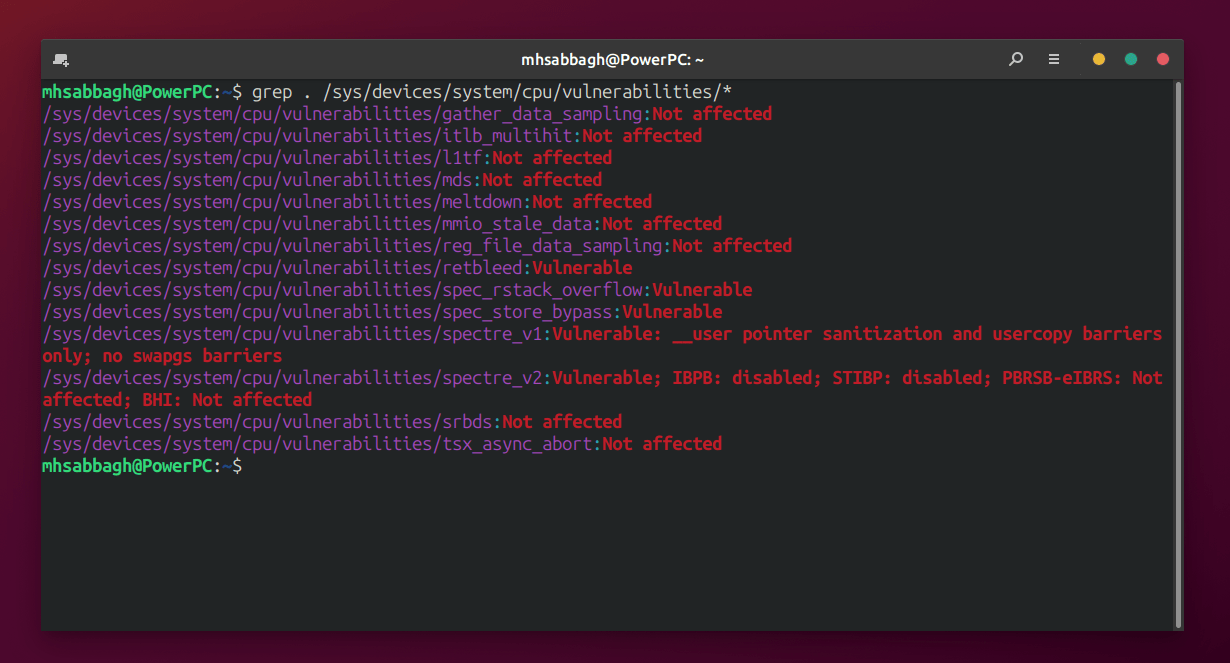
Notice how for some vulnerabilities, the output went from “Mitigation” to “Vulnerable”, indicating that our system is now vulnerable to the corresponding exploit and that the mitigations=off option is working.
Yay, our system is now hackable! 😀
You can now go and get that extra 10-20 FPS you really want in your games.
Conclusion
It is a tradeoff between security and performance gain. If you are using a modern CPU then by no means you should do this, as you don’t need it all. If you are using an older CPU (e.g. released before 2020), then even in that case you should be taking extra measures and care to not get your system hijacked when you turn off such vulnerability mitigations. If you don’t need the performance gain, then don’t do it.
So far, there aren’t reports of such exploits being exploited out in the wild on the Internet via JavaScript engines in web browsers. However, it is still theoretically possible, and you should be cautious about what websites you visit.
Remember that with great power comes great responsibility!
With a B.Sc and M.Sc in Computer Science & Engineering, Hanny brings more than a decade of experience with Linux and open-source software. He has developed Linux distributions, desktop programs, web applications and much more. All of which attracted tens of thousands of users over many years. He additionally maintains other open-source related platforms to promote it in his local communities.
Hanny is the founder of FOSS Post.